Today I want to show you several examples of controlling certificates that were published in Active Directory Ceritfication Services, with the help of simple PowerShell commands, on the example of 3 real cases.
First of all, you have to have the PSPKI module. You can install it with the command:
Install-Module -Name PSPKI
Just in case, I uploaded arhive with the module to the Yandex Drive.
Example 1. Revoke all certificates, that were published from some template, which was deleted, but we know its ID:
import-module pspki
#set your AD CS server and ID of the template
$adcsserver="adcs01.test.loc"
$template="1.3.6.1.4.1.311.21.8.13954309.9887930.9521039.15715224.4226860.116.724438.4097016"
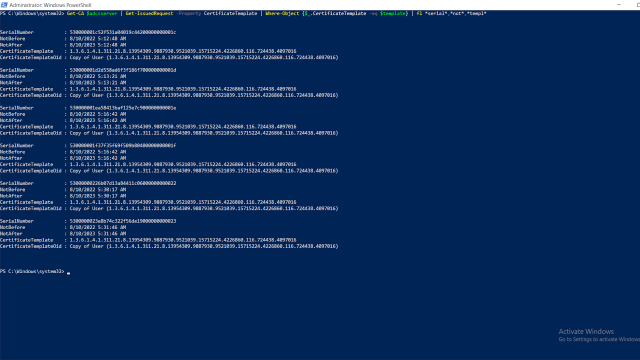
Get-CA $adcsserver | Get-IssuedRequest -Property CertificateTemplate | Where-Object {$_.CertificateTemplate -eq $template} | revoke-certificate
Example 2. Remove all certificates which were published from the same template, from AD User object (I mean from the Certificates field):
import-module pspki
import-module activedirectory
#set your AD CS server and ID of the template
$adcsserver="adcs01.test.loc"
$template="1.3.6.1.4.1.311.21.8.13954309.9887930.9521039.15715224.4226860.116.724438.4097016"
$logpath=$env:userprofile+"\documents\log.txt"
"" | out-file $logpath -encoding UTF8
#If certificates were not revoked
$certs=Get-CA $adcsserver | Get-issuedRequest -Properties CertificateTemplate,RequesterName | Where-Object {$_.CertificateTemplate -eq $template}
#If certificates are already revoked we should use get-revokedrequest
#$certs=Get-CA $adcsserver | Get-revokedRequest -Properties CertificateTemplate,RequesterName | Where-Object {$_.CertificateTemplate -eq $template}
if ($certs -ne $null){
foreach ($cert in $certs){
$username=$cert.'Request.RequesterName' -replace ".*\\",""
$user=get-aduser $username -properties usercertificate,certificates
#It is possible to limit the command with some OU, to avoid execution on all domain users
#$user=get-aduser -SearchBase "OU=users-ou,DC=test,DC=loc" -Filter {samaccountname -eq $username} -properties usercertificate,certificates
if ($user.certificates.count -gt 0){
foreach($usercert in $user.Certificates){
$certV2 = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2 $usercert
if ($certV2.serialNumber -eq $cert.serialnumber){
try{
set-aduser $user.samaccountname -certificates @{remove=$usercert} -erroraction stop
"certificate removed from AD user object - $username. Certificate SN - $($cert.serialNumber)`n" | out-file $logpath -encoding UTF8 -append
write-host "certificate removed from user ojcet - $username. Certificate SN - $($cert.serialNumber)`n"
}
catch {
$removeerror="unable to remove certificate $($certv2.serialnumber) for user $username `n"
$removeerror+=$_
$removeerror+="`n"
write-host $removeerror -foregroundcolor red
$removeerror | out-file $logpath -encoding UTF8 -append
}
}
}
}
}
}
Example 3. Export all machine certificates to the CSV file, with next fields: Requester, Subject, Not before, Not after, Issuer, ccm, rmd, template:
import-module pspki
$csvpath=$env:userprofile+"\documents\certs.csv"
#set your AD CS server and ID of the template
$adcsserver="adcs01.test.loc"
$rawcerts=Get-CA $adcsserver | Get-IssuedRequest -Properties rawcertificate,requestattributes
"requester;subject;from;to;issuer;ccm;rmd;template" | out-file $csvpath -encoding utf8
foreach ($rawcert in $rawcerts){
##for automatticaly deployed certificates
if (($rawcert.'Request.RequesterName'.ToString()) -like "*$"){
$Cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$requester=$rawcert.'Request.RequesterName'
$cert.Import([convert]::frombase64string($rawcert.rawcertificate))
$subject=$cert.subject
$from=$cert.NotBefore
$to=$cert.NotAfter
$issuer=$cert.issuer
$ccm=$rawcert.'Request.RequestAttributes' | findstr "ccm"
$rmd=$rawcert.'Request.RequestAttributes' | findstr "rmd"
$template=$rawcert.certificatetemplate
$requester+";"+$subject+";"+$from+";"+$to+";"+$issuer+";"+$ccm+";"+$rmd+";"+$template | out-file $csvpath -append -encoding utf8
}
##If you have to get information for certificates which were requested by a user, for example those from IIS console, you can use template names
elseif ($rawcert.certificatetemplate -like "*WebServer*"){
$Cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$requester=$rawcert.'Request.RequesterName'
$cert.Import([convert]::frombase64string($rawcert.rawcertificate))
$subject=$cert.subject
$from=$cert.NotBefore
$to=$cert.NotAfter
$issuer=$cert.issuer
$ccm=$rawcert.'Request.RequestAttributes' | findstr "ccm"
$rmd=$rawcert.'Request.RequestAttributes' | findstr "rmd"
$template=$rawcert.certificatetemplate
$requester+";"+$subject+";"+$from+";"+$to+";"+$issuer+";"+$ccm+";"+$rmd+";"+$template | out-file $csvpath -append -encoding utf8
}
}
Share the article with your friends in social networks, maybe it will be useful to them.
If the article helped you, you can >>thank the author<<







