Hello there! Today, I’m going to demonstrate a unique way of routing with Linux tools. We'll learn how to direct traffic through different gateways based on its origin and destination. This can be handy for creating a double VPN, speeding up certain website loads, especially in regions with internet restrictions like China.
Key Tools We'll Use:
- Policy based routing
- Dnsmasq
- Ipset
Our setup will be on an Ubuntu Server 16.04. For demonstration purposes, I'll show how you can use a PPTP server (optional) to set up a double VPN for certain websites.
Network Setup:
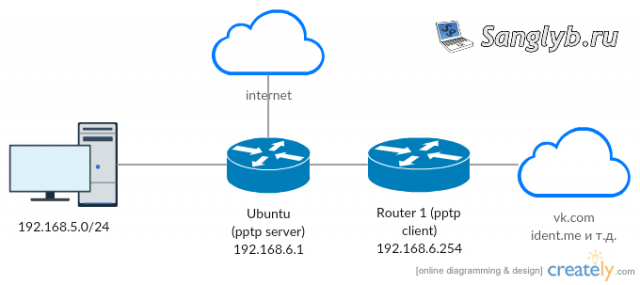
A client, located in the network 192.168.5.0/24, connects via PPTP to our Ubuntu Server (192.168.6.1). Upon sending a request, the server checks the destination address. If the address is in our database, it routes to the gateway - router 1, with address 192.168.6.254. Otherwise, it uses the default gateway.
Implementation Steps:
Initial Configuration:
- Go into superuser mode with
sudo su
- Update and install the necessary packages:
apt update apt upgrade apt install ipset dnsmasq
Setting Up Ipset:
- Create a list for ipset with a possible timeout for entries:
ipset create to2ndSRV hash:ip
- If you need to manually add an address to the list, use:
ipset add to2ndSRV 8.8.8.8
- And for removal:
ipset del to2ndSRV 8.8.8.8
- To view the list:
ipset list to2ndSRV
Fine-tuning Dnsmasq:
- For adding resources that have many addresses, you can use dnsmasq. Configure dnsmasq by editing
/etc/dnsmasq.confand adding the necessary directives.
nano /etc/dnsmasq.conf
listen-address=127.0.0.1
listen-address=192.168.6.1
server=/ident.me/vk.com/127.0.0.1
ipset=/ident.me/vk.com/to2ndSRV
- The initial lines ensure dnsmasq doesn't reveal itself externally to avoid abuse reports. For consistency in address additions, DNS queries should route through dnsmasq. The simplest method is by setting our server (192.168.6.1) as the DNS server on the client.
- Restart dnsmasq:
/etc/init.d/dnsmasq restart
- Check that the addition of resources is working correctly:
host ident.me ipset list
The output should be similar to (ident.me address should be added to the list):
Name: to2ndSRV
Type: hash:ip
Revision: 4
Header: family inet hashsize 1024 maxelem 65536 timeout 3600
Size in memory: 320
References: 0
Members:
176.58.123.25 timeout 3594
Traffic Routing:
- To ensure traffic routes to the appropriate gateway based on the address in our list, edit the scripts for raising and lowering the interface, specifically,
/etc/ppp/ip-upand/etc/ppp/ip-down. - If the second router is unavailable, the traffic should go directly via the default gateway. Thus, remember to edit both mentioned files appropriately.
- To ensure traffic routes to the appropriate gateway based on the address in our list, edit the scripts for raising and lowering the interface, specifically,
nano /etc/ppp/ip-up
Add lines to the end of the file:
case "$5" in 192.168.6.254) echo 2 > /proc/sys/net/ipv4/conf/$1/rp_filter /sbin/ip route add default via 192.168.6.254 table 120 /sbin/ip rule add fwmark 0x1 table 120 priority 1000 ip route fush cache iptables -t mangle -A PREROUTING -s 192.168.5.0/24 -m set --match-set to2ndSRV dst -j MARK --set-mark 1 iptables -t nat -A POSTROUTING -o $1 -j MASQUERADE ;; *) esac
Some details about the script:
echo 2 > /proc/sys/net/ipv4/conf/$1/rp_filter — Disables the route policy filter. It's an undesirable line, but without it, things didn't work for me.
iptables -t mangle -A PREROUTING -s 192.168.5.0/24 -m set --match-set to2ndSRV dst -j MARK --set-mark 1 — Here, we add a mangle rule in iptables for packet marking. If the destination address is present in ipset, the packet is marked.
/sbin/ip route add default via 192.168.6.254 table 120 — We create a new routing table to direct traffic to our second router.
/sbin/ip rule add fwmark 0x1 table 120 priority 1000 — We add a rule to the created routing table, so marked packets are directed to our second router.
ip route flush cache — Clear the cache.
iptables -t nat -A POSTROUTING -o $1 -j MASQUERADE — We perform Network Address Translation (NAT) for traffic to our second router.
Edit second file:
nano /etc/ppp/ip-down
case $5 in 192.168.6.254) ip rule delete fwmark 0x1 table 120 priority 1000 ip route delete default via 192.168.6.254 table 120 ip route flush cache iptables -t mangle -D PREROUTING -s 192.168.5.0/24 -m set --match-set to2ndSRV dst -j MARK --set-mark 1 iptables -t nat -D POSTROUTING -o $1 -j MASQUERADE ;; *) esac
Client and Router Setup:
- Add a user for the client and second router by editing
/etc/ppp/chap-secrets, and restart PPTP.
- Add a user for the client and second router by editing
nano /etc/ppp/chap-sercets
test1 pptpd testtest 192.168.5.100
srv pptpd testtest 192.168.6.254
/etc/init.d/pptpd restart
Testing:
After setup, connect with the client and router. From the client, perform a traceroute to a resource from your list. For instance, you might see that packets to a site like ident.me may pass through our gateway, whereas others might go directly.
traceroute to ya.ru (87.250.250.242), 30 hops max, 60 byte packets
1 192.168.6.1 (192.168.6.1) 1.120 ms 1.064 ms 1.048 ms
2 * * *
3 192.168.55.1 (192.168.55.1) 4.209 ms 4.237 ms 4.233 ms
4 10.45.0.1 (10.45.0.1) 6.014 ms 6.008 ms 6.285 ms
traceroute to ident.me (176.58.123.25), 30 hops max, 60 byte packets
1 192.168.6.1 (192.168.6.1) 1.136 ms 1.171 ms 1.166 ms
2 cs01.et-code.ru (192.168.6.254) 8.188 ms 8.183 ms 8.179 ms
3 * * *
4 192.168.55.1 (192.168.55.1) 26.074 ms 26.123 ms 26.119 ms
5 10.45.0.1 (10.45.0.1) 30.085 ms 30.198 ms 30.195 ms
Conclusion:
This Linux-based routing method provides more flexibility in managing and directing your traffic, ensuring faster load times and overcoming region-based restrictions. It's a valuable tool for anyone looking to optimize their network's efficiency.
Share the article with your friends in social networks, maybe it will be useful to them.
If the article helped you, you can >>thank the author<<







